Third-Party API Visibility

Know what data goes where, when, and how across third-party apps.
Third-party breaches grew 68% in 2023.
Get continuous visibility into third-party API communications involving third-party apps handling sensitive data.
Source: Verizon DBIR 2023
Eric Richard
Dutchie, CISO (formerly HubSpot CISO)
"I think most CISOs already know this, but third-party APIs are right now probably one of the Achilles heels of our world, with a very wide usage and almost no visibility unto them. The goal, through a tool like Vorlon, is you can bring that out of the shadows and into the light and can start to put the same sorts of controls in API security that we’ve put on all sorts of other security over the last decades."
Jamie Brown
Vivun, CISO
"Vorlon gives us greater visibility across all third-party API assets and dramatically reduced event triage timelines."
Avishai Avivi
SafeBreach, CISO
"Vorlon helped us understand not just the APIs we were using but also what systems these APIs were connecting to and the data that was enabled on top of the APIs. Vorlon provided me with quite a bit of telemetry and threat intel around our API usage — which is especially game-changing for the third parties that might as well be a black box to us. The biggest takeaway for us is the sheer size of the attack surface generated by third-party vendors connecting to our data both directly and indirectly."
Monitor Your Data in Motion
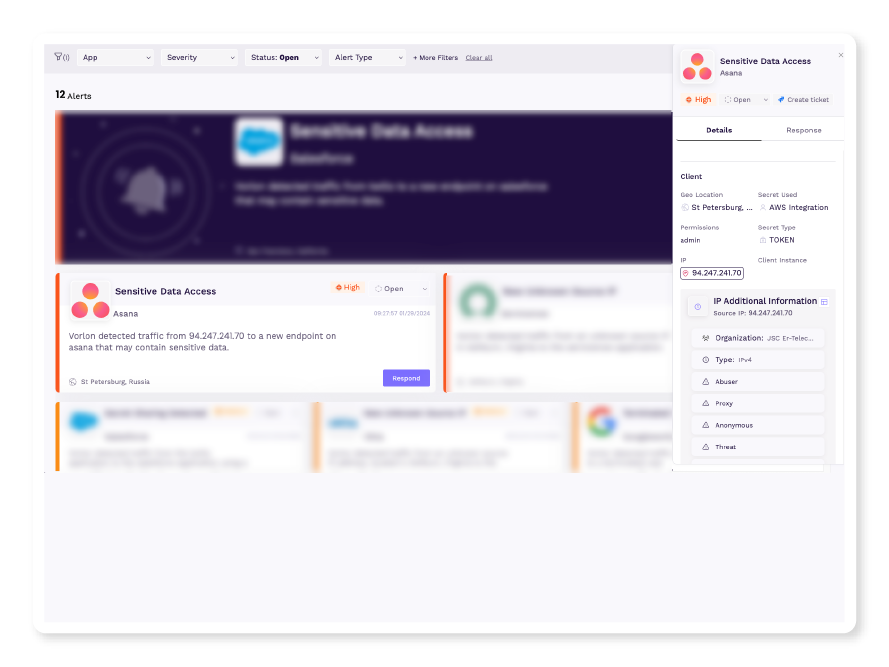
Vorlon continuously monitors API communications and usage between your organization’s third-party apps and detects unusual or suspicious activities.
For security/incident response teams to monitor third-party API usage.
Detect unusual patterns of activity or behavior with near real-time API anomaly detection.
Investigate faster with enriched threat intelligence, including malicious IP address identification.
Stay informed with immediate alerts when suspicious or anomalous activities are detected in API communications.
MITRE ATT&CK® for Third-Party APIs
Today's attacks increasingly leverage your unmonitored third-party API connections.
Below are the tactics and techniques representing the MITRE ATT&CK® Matrix for Enterprise.
| Recon | Initial Access | Collection | Data Theft | Extortion |
|
Attacker performs reconnaissance using publicly available data sources and previous breach information available on the dark web. |
Attacker gains access to systems leveraging legitimate API Secrets that connect two or more vendor applications used by the target. | Attacker makes one or more API calls to the target’s vendor application. | Attacker is able to pull data, which is decrypted because the attacker is using a legitimate API secret. | Once sufficient valuable data is stolen, the attacker extorts the target. |
It all starts with observing data in motion.
Continuously Monitor
Start by observing third-party apps consumption of your data in near real-time. Don't check in periodically because it might be too late.
Identify App-to-App Connections
Know what is going where and when. Vorlon can identify thousands of applications connecting to your data.
Secrets Inventory
Understand the lifecycle, usage, and behavior of your third-party secrets with a comprehensive inventory.
Find IOCs through behavioral alerts and enhanced threat intel.
Abnormal Behavior
It is entirely possible to have a third-party app correctly configured, the access token be stolen, and then that over-permissive access abused by an attacker. When Vorlon alerts immediately upon detecting something abnormal.
Investigate
It's hard to investigate what's going on between two third-party applications your organization doesn't control. Vorlon enhances threat intel by providing additional context not found in third-party logs.
Fix in 2 Clicks
Respond and revoke access directly within Vorlon or generate a ticket by connecting Vorlon with your ITSM.

Whitepaper
Navigating the Risks and Rewards of Third-Party Apps
Includes free Third-Party Security Incident Contingency Plan worksheets to guide CISOs and SecOps leaders through the gap identification process.