About The Platform
Vorlon
Vorlon is the first easy way to secure complex SaaS ecosystems. With Vorlon, your SaaS gets proactive security coverage like you have for your endpoints and cloud. After an agentless, proxy-free setup, you can monitor sensitive data flows, manage secrets, detect anomalies, and revoke access.
Fast Time-To-Value
Select the app you want to observe from our catalog and enter either a read-only API key, or initiate an OAuth flow. Within minutes, you'll know who your SaaS applications are talking to and who's talking to them.
Reduce Your Time to Detect
Reduce Your Time to Respond
Reduce Your Attack Surface
Continuous Monitoring
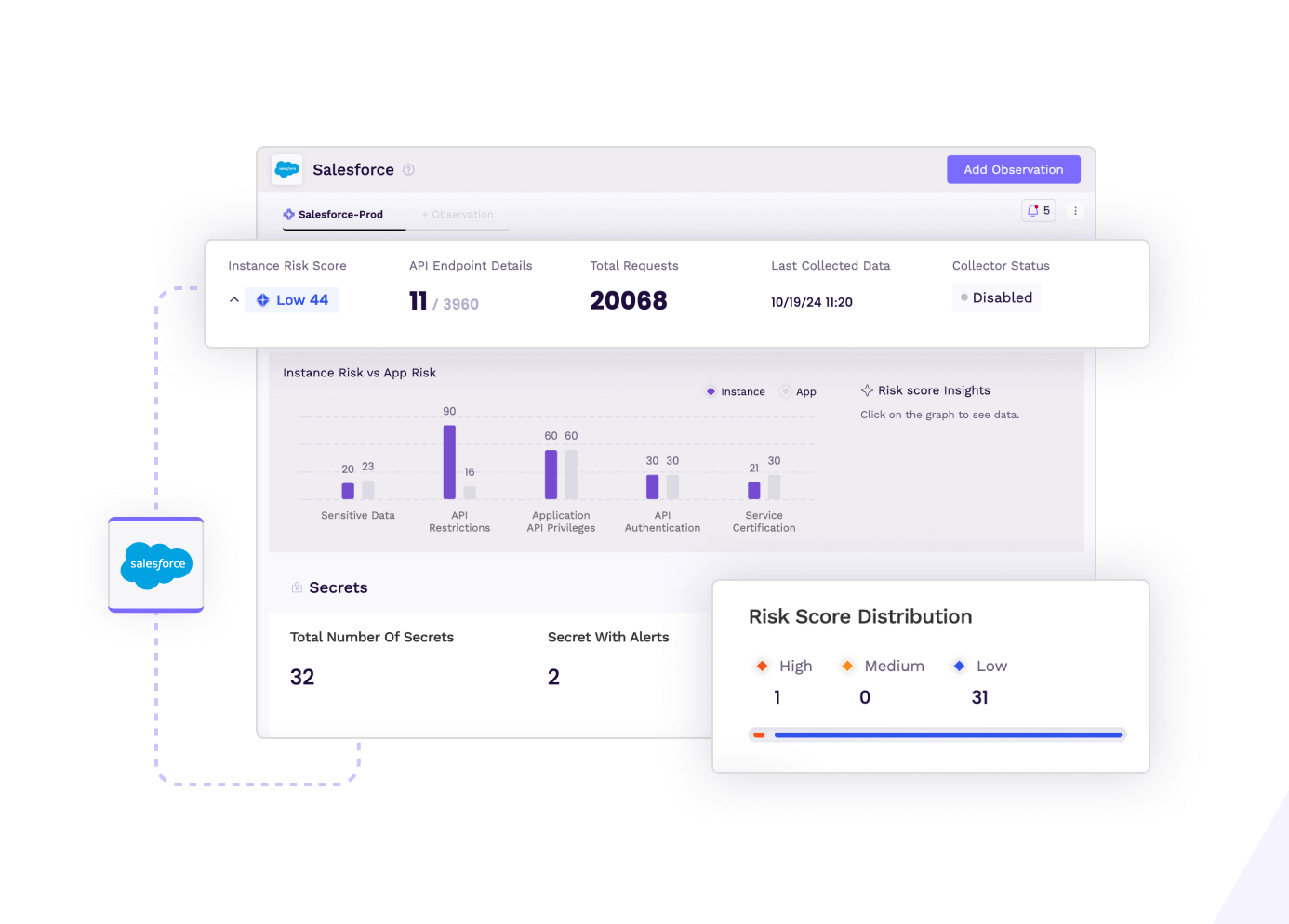
Understand your risk with continuous risk scoring for all SaaS applications, secrets, and users.
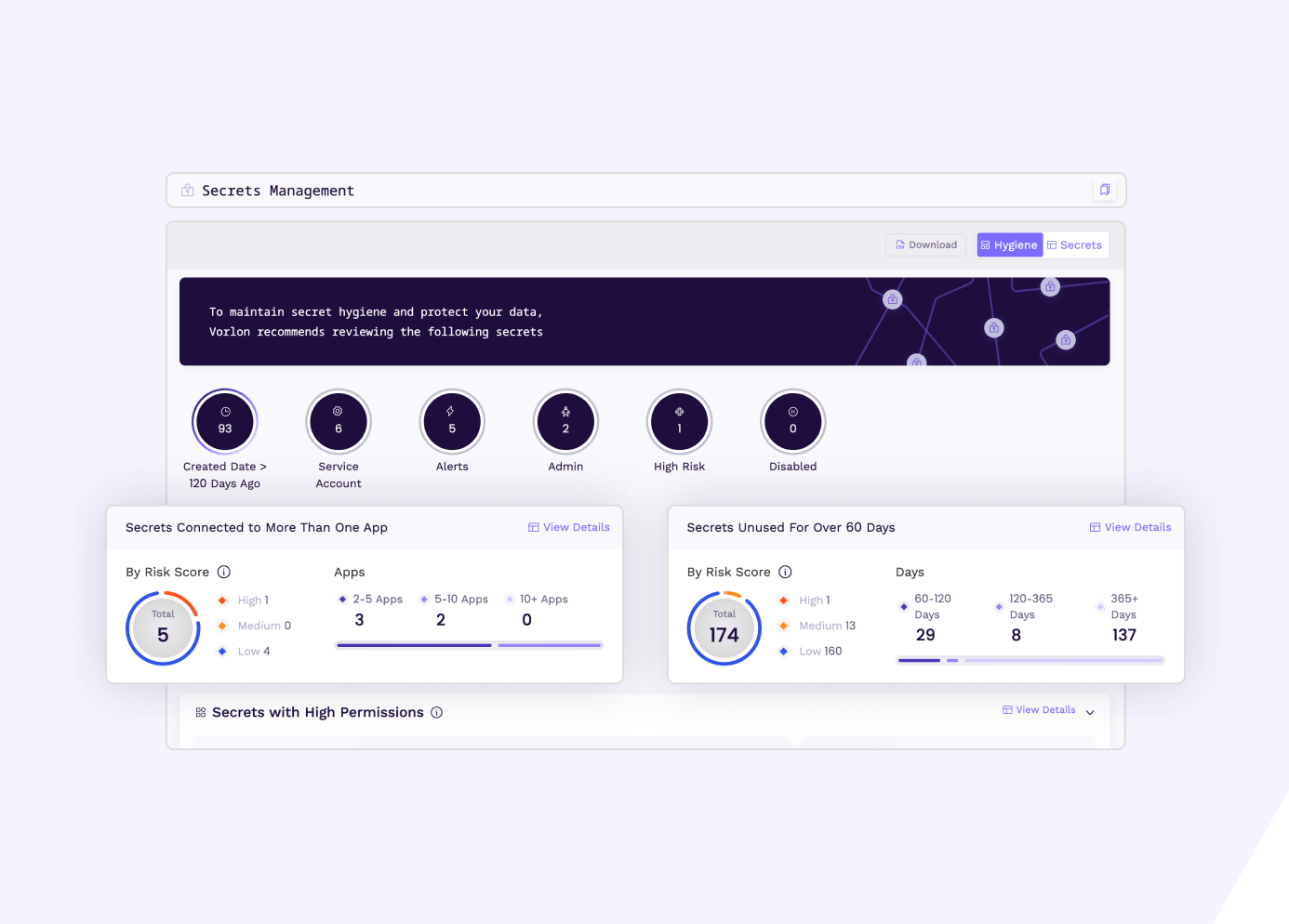
Secrets Management
Monitor all your secrets’ metadata and activity. Understand the lifecycle, usage, and behavior of your secrets with a comprehensive inventory.
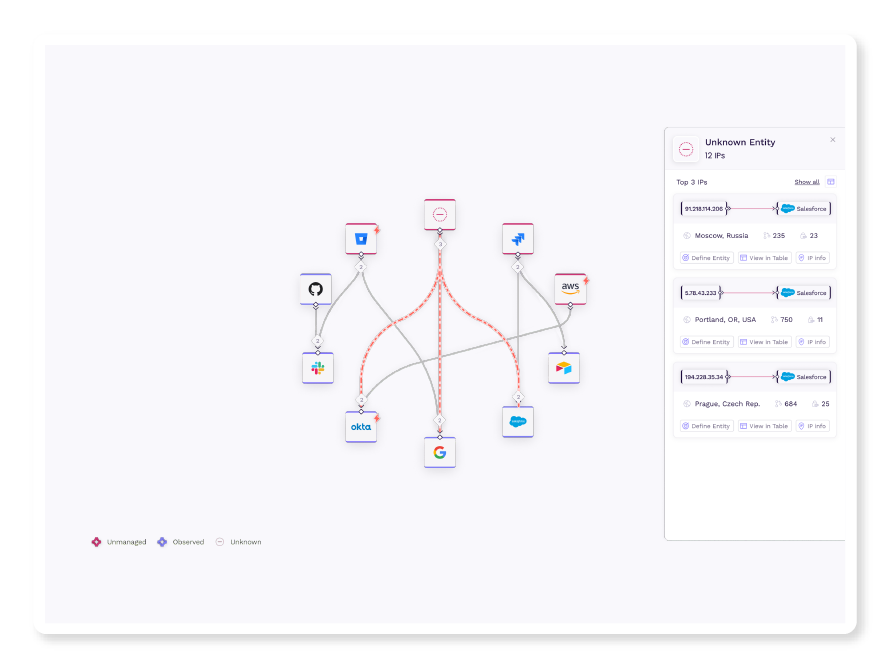
Threat Investigation
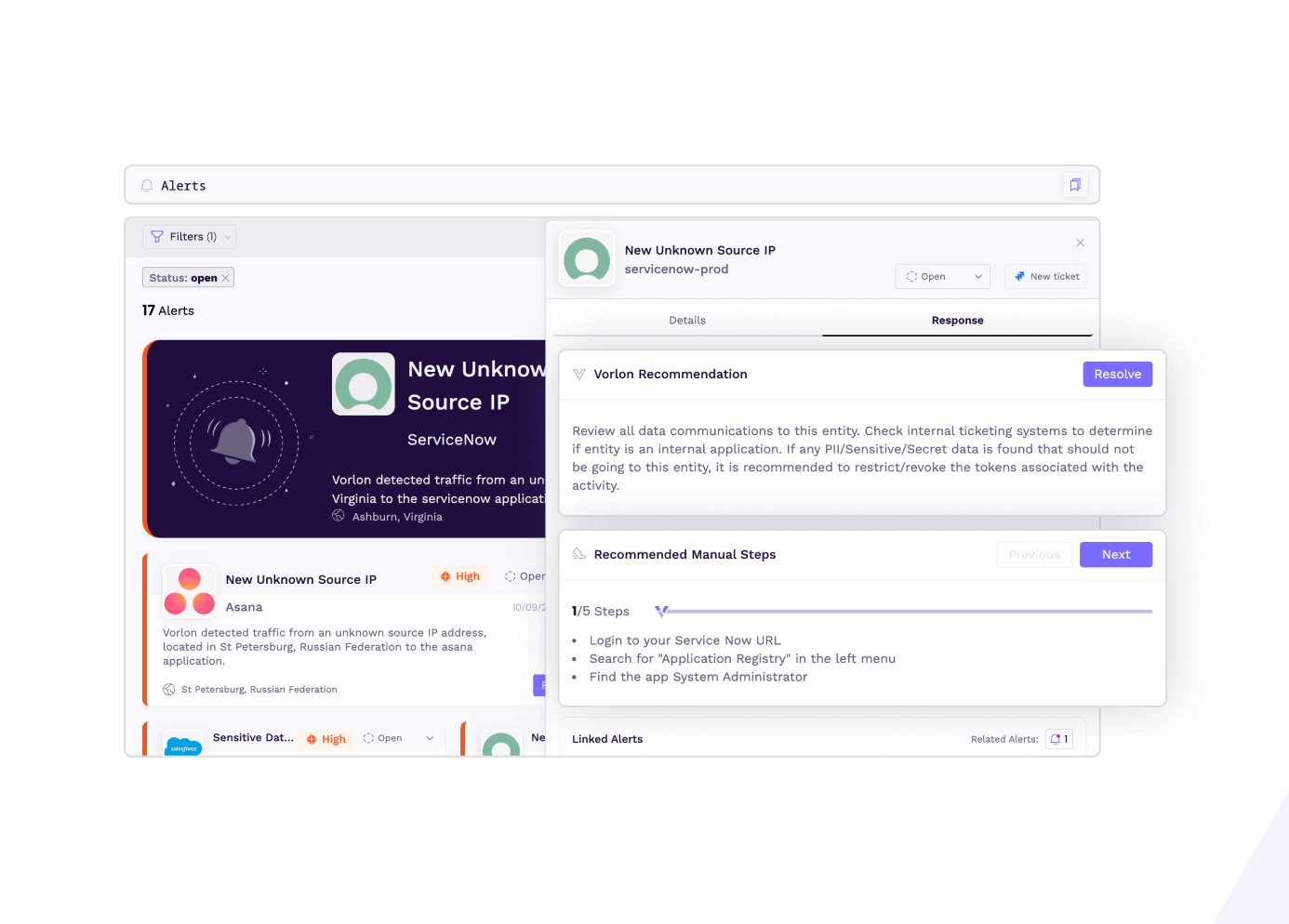
Get alerted to anomalous connections into your SaaS apps. Malicious IP address identification is built directly into Vorlon for faster threat investigations.
Real-Time Data Analysis
Continuously monitor and analyze the data flows between your organization’s SaaS apps in near real-time. Vorlon detects anomalies for malicious and inappropriate activity.
Compliance Violation Prevention
Reduce fines from costly compliance violations by proactively managing access to sensitive SaaS data. Quickly correct potential issues before they become violations with continuous monitoring and behavioral notifications.
Behavioral Alerts
All apps have a behavioral baseline of normal, valid traffic. Know immediately when something isn't right with alerts sent in-app, or via SMS, Slack, or Microsoft Teams.
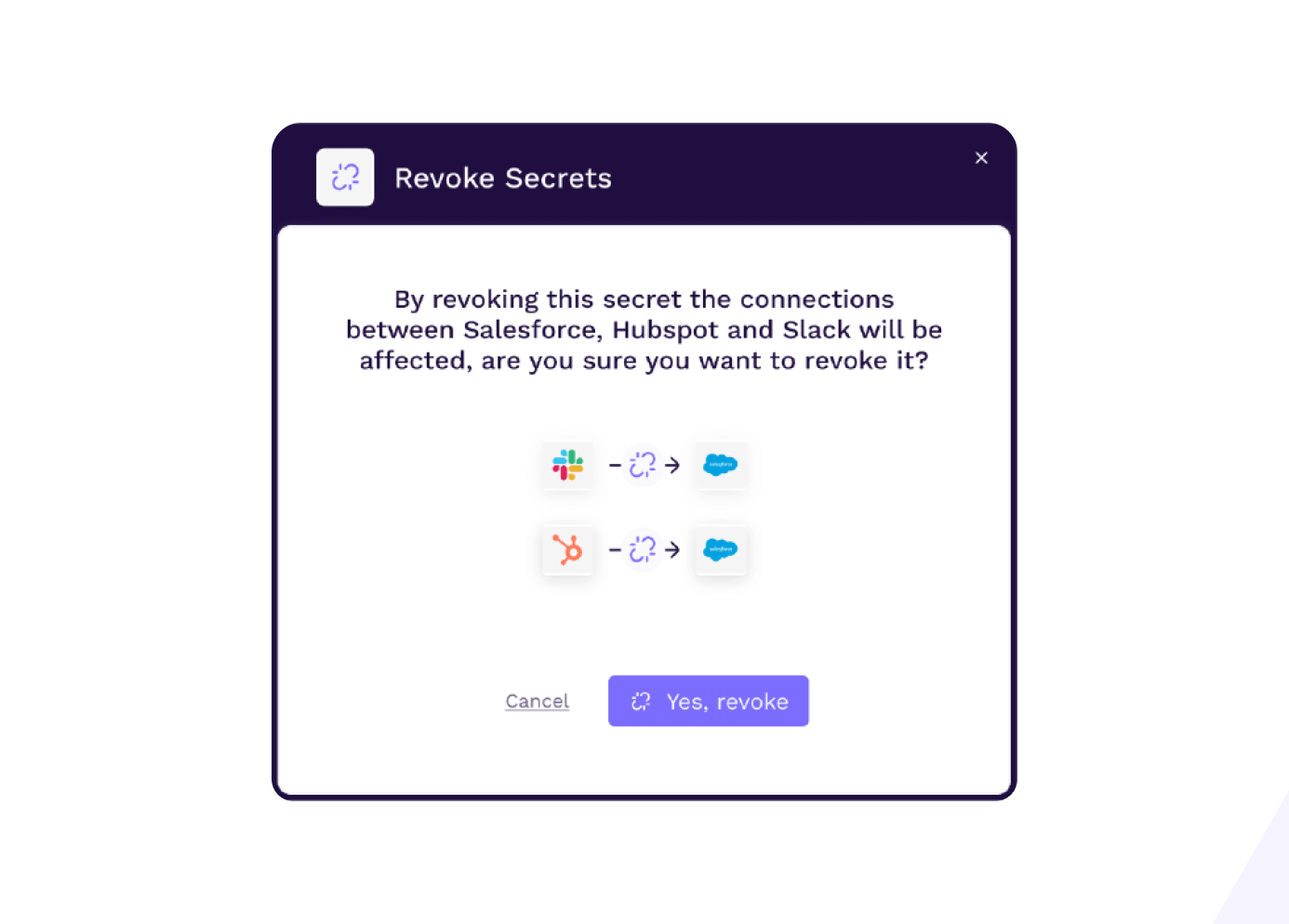
Fix with Two Clicks
Respond to security incidents within minutes, not months. Revoke or rotate secrets within the Vorlon platform.
Features
Dashboard
View a comprehensive summary of your SaaS apps, secrets, and data, including in-depth insights into trends and what requires your immediate attention.
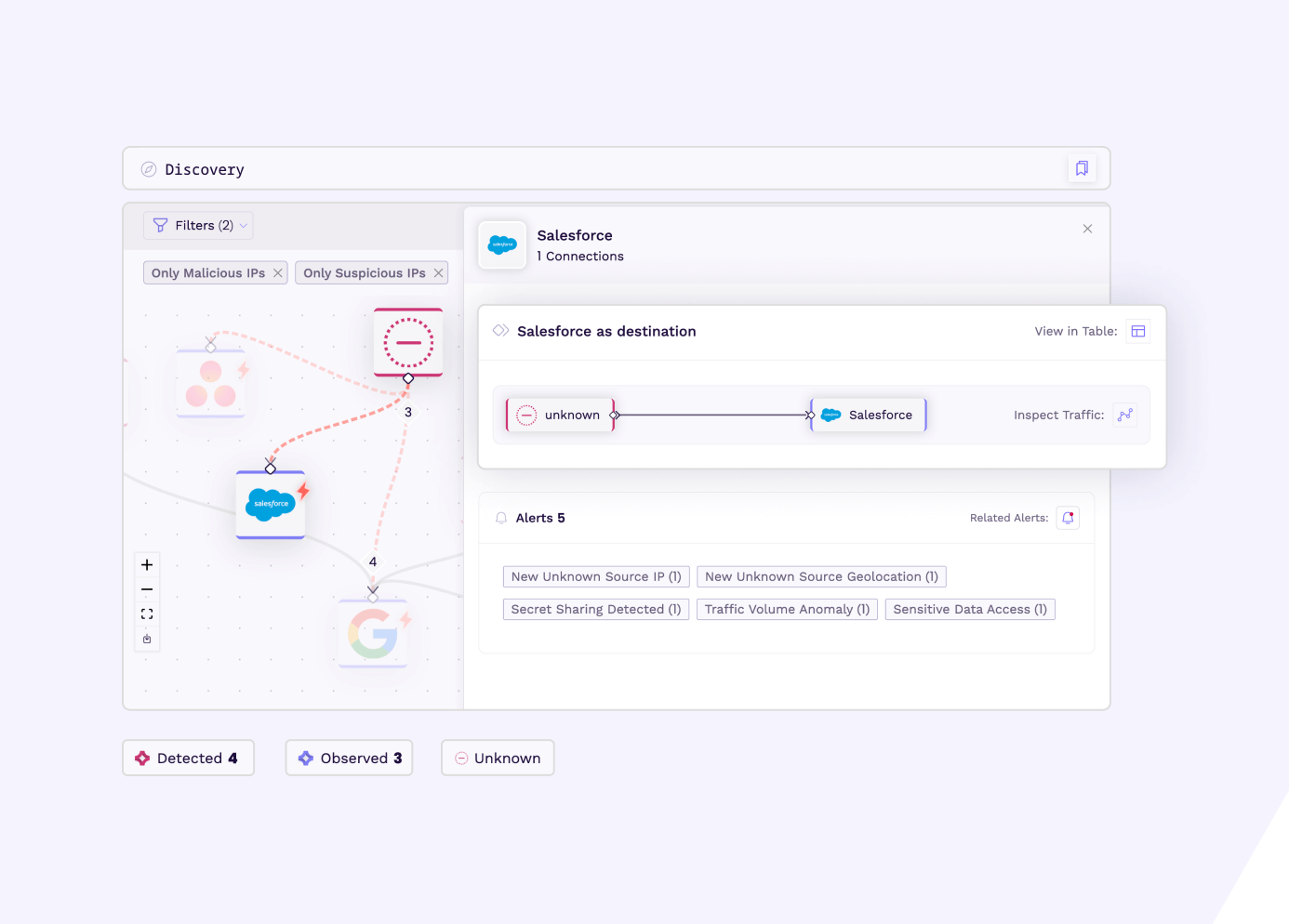
Discovery
Discover all connected applications and services. Drill down into their connections and analyze traffic for detailed investigations.
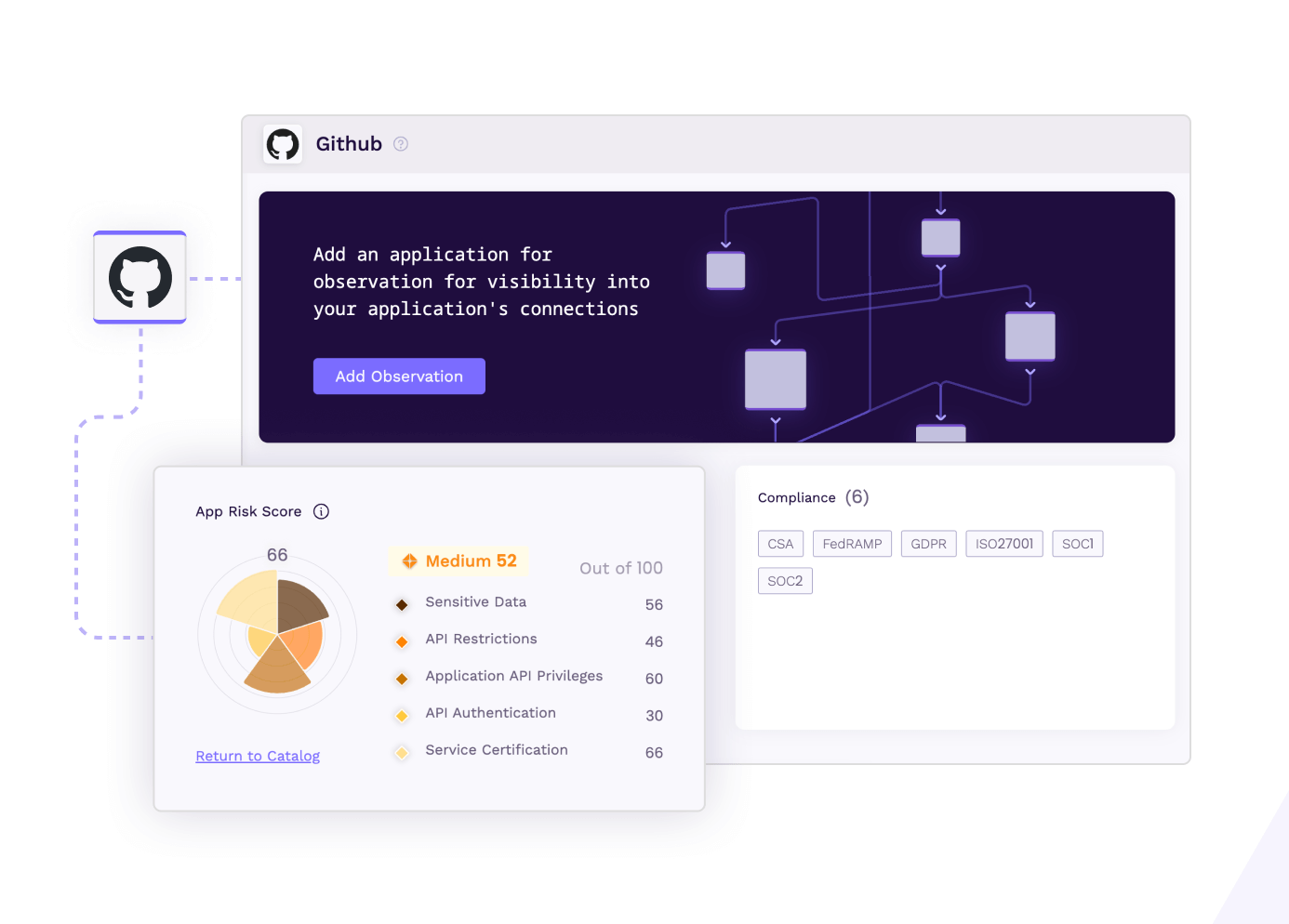
Risk Profile
Configure observed apps and tag sensitive data. See risk scoring and compliance for each SaaS vendor and benchmark your instance of their app.
Secrets
See an inventory of all SaaS secrets, including permissions and metadata. Manage secrets by tagging, adding notes, or revoking.
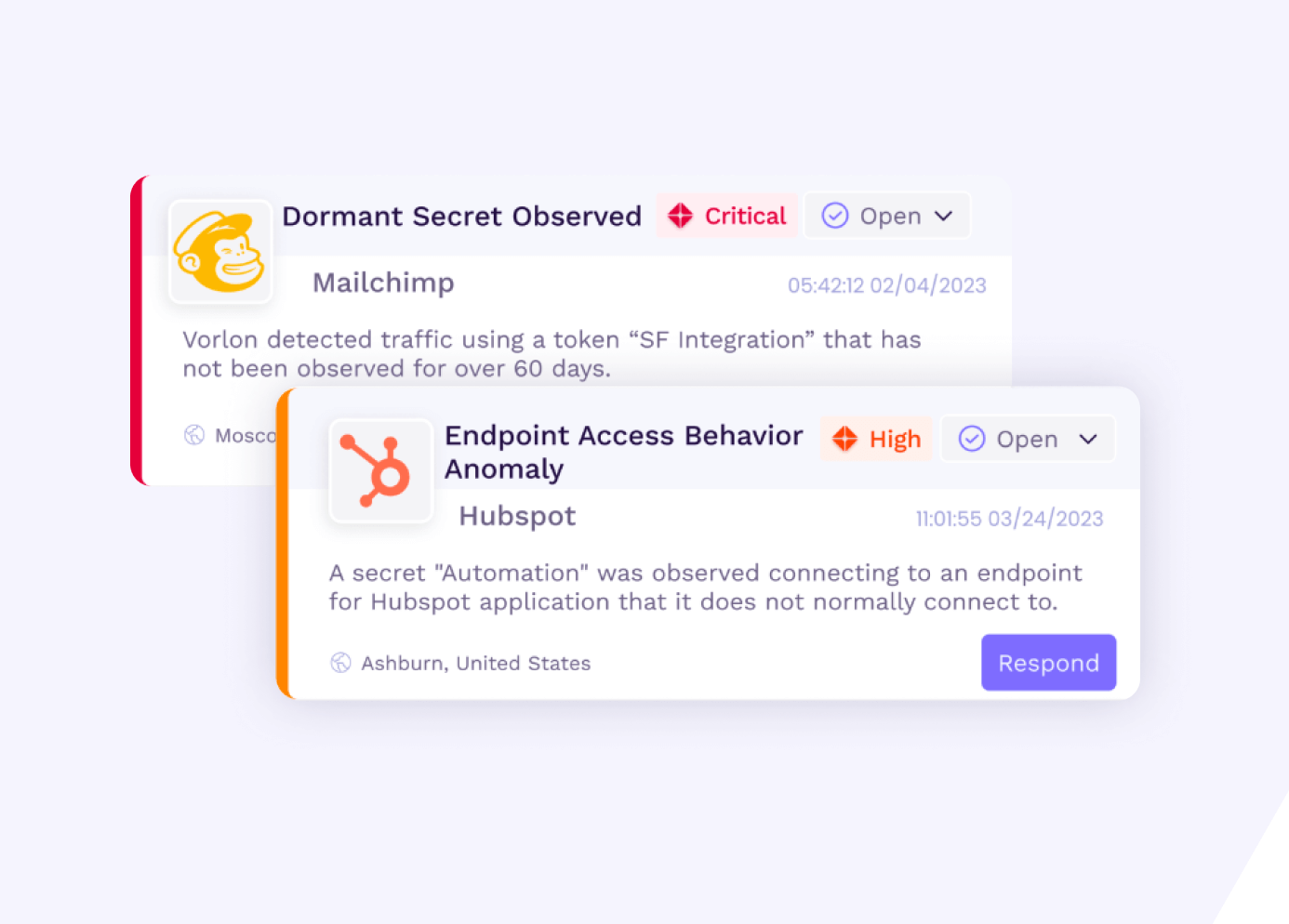
Alerts
View and manage real-time alerts in a user-friendly interface. Detailed response recommendations are provided for each alert.
Ask Vorlon
Your AI Advisor knows and learns your SaaS ecosystem. Ask it anything you want about your apps, secrets, and data.
What the Experts Say
Legendary SANS Institute DFIR Expert Takes First Look at Vorlon
Jason Jordaan, one of the most famous digital forensics and incident response instructors shares his perspective on Vorlon for security analysts in his First Look review.
This report provides an agnostic opinion of Vorlon and was written by SANS Institute with the express purpose of articulating the perceived value for a cybersecurity practitioner.
- Compliance and Protecting Your Data
- Visibility of Your Third-Party API Ecosystem
- Threat Detection and Incident Response