Secret Lifecycle Management
Manage all third-party secrets all in one place.

Monitor and Manage All Third-Party Secrets
Managing third-party secrets (API keys, credentials, OAuth) is a complicated task burdened by manual processes. Many organizations default to using spreadsheets for this purpose, which only provide a snapshot in time.
Without proper oversight over these critical access points, organizations can be exposed to potential unauthorized access and data breaches.
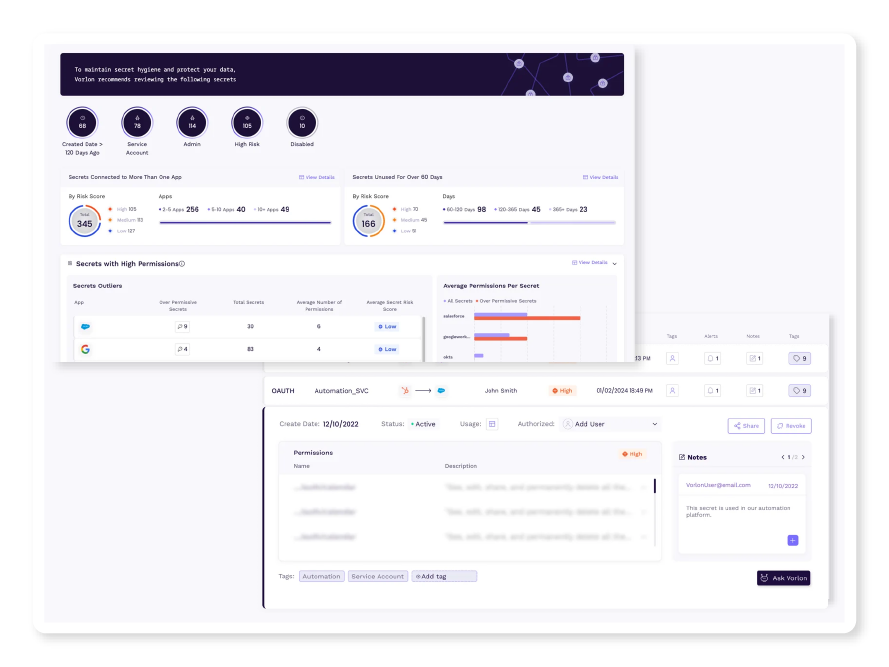
Secrets Monitoring
Vorlon monitors all your third-party secrets’ metadata and activity. Understand the lifecycle, usage, and behavior of your third-party secrets with a comprehensive secret inventory.
For security/incident response teams and application owners to manage third-party secrets.
Understand secret usage with metadata and activity tracking, including last used time, owner, and permissions.
Identify anomalous secret activity or misuse with behavioral analysis and alerting.
Enhance third-party secret inventory with custom tagging and detailed notes.
Secrets Rotation
Vorlon continuously monitors secret activity and hygiene and provides you with the capability to revoke the secret or respond efficiently through streamlined actions.
For security/incident response teams and application owners to revoke and rotate secrets.
Identify anomalous behavior, bad hygiene, or misconfiguration of secrets.
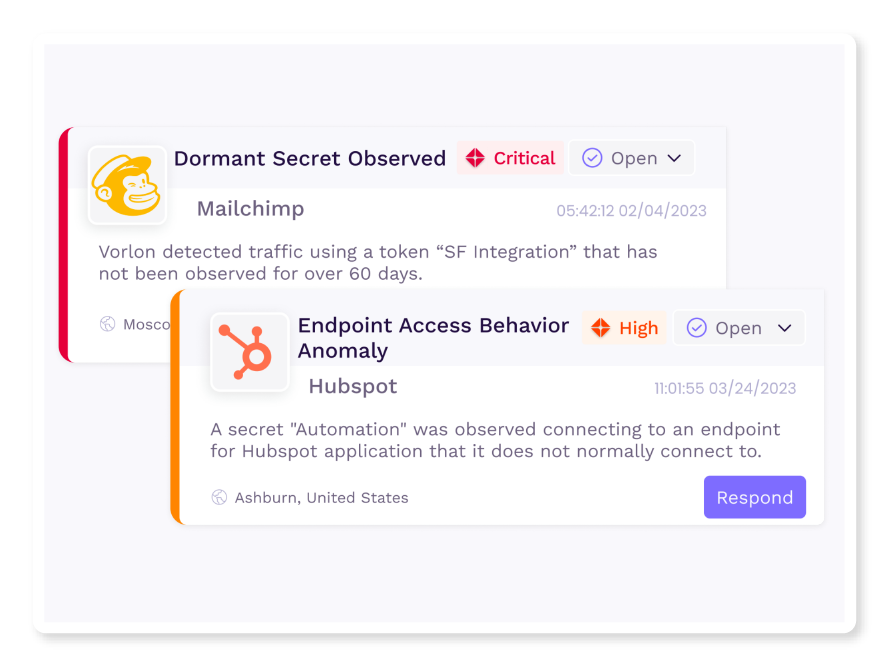
Revoke and rotate secrets seamlessly without operational disruption.
Respond efficiently to alerts by leveraging customized response recommendations tailored to each third-party app.
.png)
Secret Inventory, Better Than a Spreadsheet
Security Teams
Save time and let Vorlon identify and monitor all your third-party app secrets, enabling you to manage the entire lifecycle of all secrets. Vorlon enhances the security of all secrets, reduces risk, and ensures seamless revocations.