Third-Party Threat Hunting
Identify malicious activity in the third-party apps used by your organization in minutes—not months.

Less Time Digging Through Logs. More Time Knowing Your Third-Party Apps are Secure.
Third-party audit logs are hard to read and even harder to correlate. This complexity makes it time consuming to understand the full scope of the apps, their access secrets, and data flows.
Vorlon decreases the time it takes to find IOCs in the third-party apps with access to to your organization's data.
Attacker Window of Opportunity
By not continuously monitoring third-party APIs, you inadvertently grant attackers an average of three months to act before you might detect and remediate an issue.
Close the Window with Vorlon
Vorlon continuously monitors your third-party applications and detects abnormal behavior in near real-time, processing your data every hour. Revoke access with two clicks of a button within the Vorlon platform.
Continuous Proactive Detection
Vorlon continuously monitors your third-party API logs to proactively hunt for abnormal behavior, hidden security issues, and risks to sensitive data.
For security/incident response teams to discover, scope, and investigate incidents.
Vorlon enriches log data with threat intelligence, layering additional information to shorten research time.
Understand where your organization’s sensitive data is flowing and quickly identify affected data when a breach happens.
Search for IOC activity and identify affected accounts and secrets.
.png?width=2000&height=1124&name=TPDR-Breach-Scoping-and-Investigation%20(1).png)
Event-Driven Third-Party Alerts
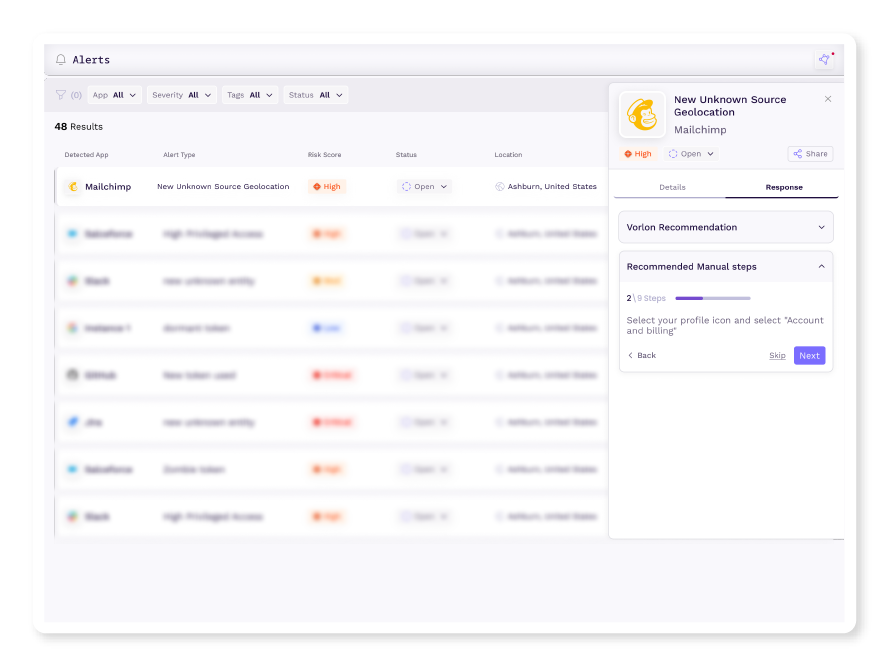
Don't wait for security researches to put out CVEs and thoroughly investigated breaches after the fact. Proactively address third-party incidents by continuously monitoring all your third-party apps. Vorlon detects abnormal behaviors with the power of AI and intelligent algorithms by analyzing your third-party apps' logs. Then, remediate issues by following step-by-step response plans or use precise automated actions.
For security/incident response teams to respond to incidents involving third-party apps, secrets, and data.
Detect anomalies in third-party app/secret/data usage with behavioral alerting.
Quickly respond to alerts with tailored response steps or automated response actions.
Don't be surprised if your security team discovers a possible third-party incident before the vendor discovers it themselves.
Jamie Brown
Vivun, CISO
"Vorlon gives us greater visibility across all third-party API assets and dramatically reduced event triage timelines."
Avishai Avivi
SafeBreach, CISO
"Vorlon helped us understand not just the APIs we were using but also what systems these APIs were connecting to and the data that was enabled on top of the APIs. Vorlon provided me with quite a bit of telemetry and threat intel around our API usage — which is especially game-changing for the third parties that might as well be a black box to us. The biggest takeaway for us is the sheer size of the attack surface generated by third-party vendors connecting to our data both directly and indirectly."
Eric Richard
Dutchie, CISO (formerly HubSpot CISO)
"I think most CISOs already know this, but third-party APIs are right now probably one of the Achilles heels of our world, with a very wide usage and almost no visibility unto them. The goal, through a tool like Vorlon, is you can bring that out of the shadows and into the light and can start to put the same sorts of controls in API security that we’ve put on all sorts of other security over the last decades."
Anthony Lee-Masis
CISO and Data Privacy Officer
"Every few years, cybersecurity undergoes a transformation to safeguard what's truly invaluable. As businesses increasingly embrace third-party solutions, it's crucial to monitor the data flowing between them. Enter Vorlon, a solution designed to empower businesses with the essential visibility and proactive security measures needed to protect their most valuable assets."
Steve Loughlin
Accel, Partner
"The patent-pending technology Vorlon has built is far superior to anything else we have seen in this space."
Reduce Time to Detect & Remediate
Near Real-Time
Automatic detection of abnormal API behavior with your vendors.
SIEM Integrations
Remediate within Vorlon or push to your ITSM.
Real-time Risk Ratings
We all know SOC audits can be falsified; know for real in real-time.
Find the Issue and Respond
Security Teams
Gain visibility into your third-party apps and understand the data that flows between them. Detect, investigate, and respond to abnormal third-party app activity, data breaches, and security incidents in near real-time.
Learning Resources
SANS First Look: Third-Party API Security with Vorlon
