Know Where Your Sensitive Data Flows
SaaS audit logs are hard to read and even harder to correlate. When there's a breach, this complexity hinders your understanding of the access, users, secrets, and sensitive data involved in the breach or security incident.
Attacker Window of Opportunity
If you're not continuously monitoring SaaS APIs, you could be granting attackers an average of three months to act before you detect and remediate an issue.
Close the Window with Vorlon
Vorlon continuously monitors your SaaS ecosystem and detects abnormal behavior. Quickly assess the situation, alert app owners, and revoke access in just two clicks.
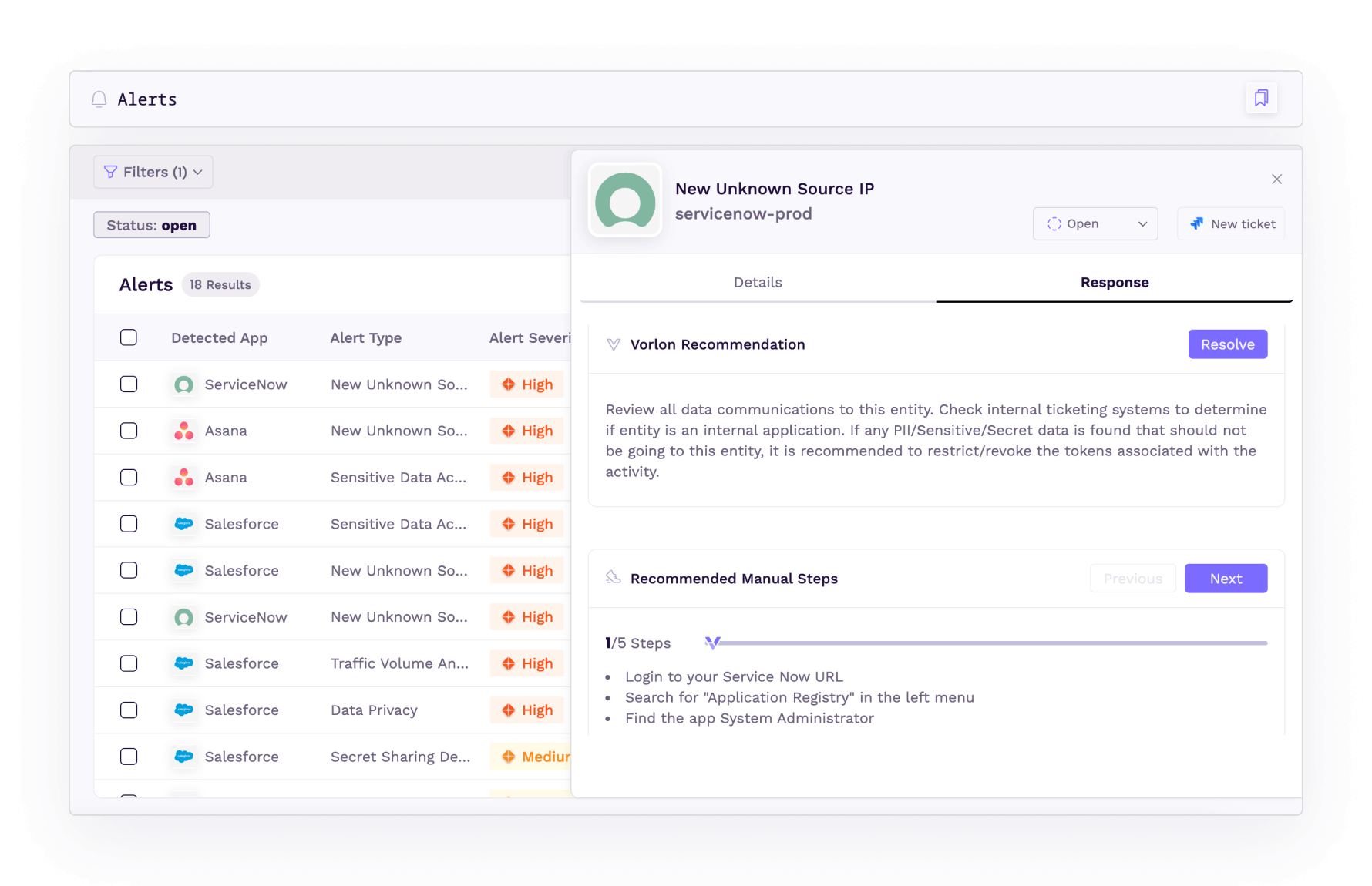
SaaS Incident Response
When a SaaS vendor tells you they were breached, it can be hard to know how to respond. But why wait for them to tell you in the first place?
Behavioral alerting lets you know when it's time to act.
Quickly respond to incidents involving SaaS apps, users, secrets, and sensitive data.
Get step-by-step remediation guidance, or kick off an automation in your SIEM, SOAR, or ITSM.
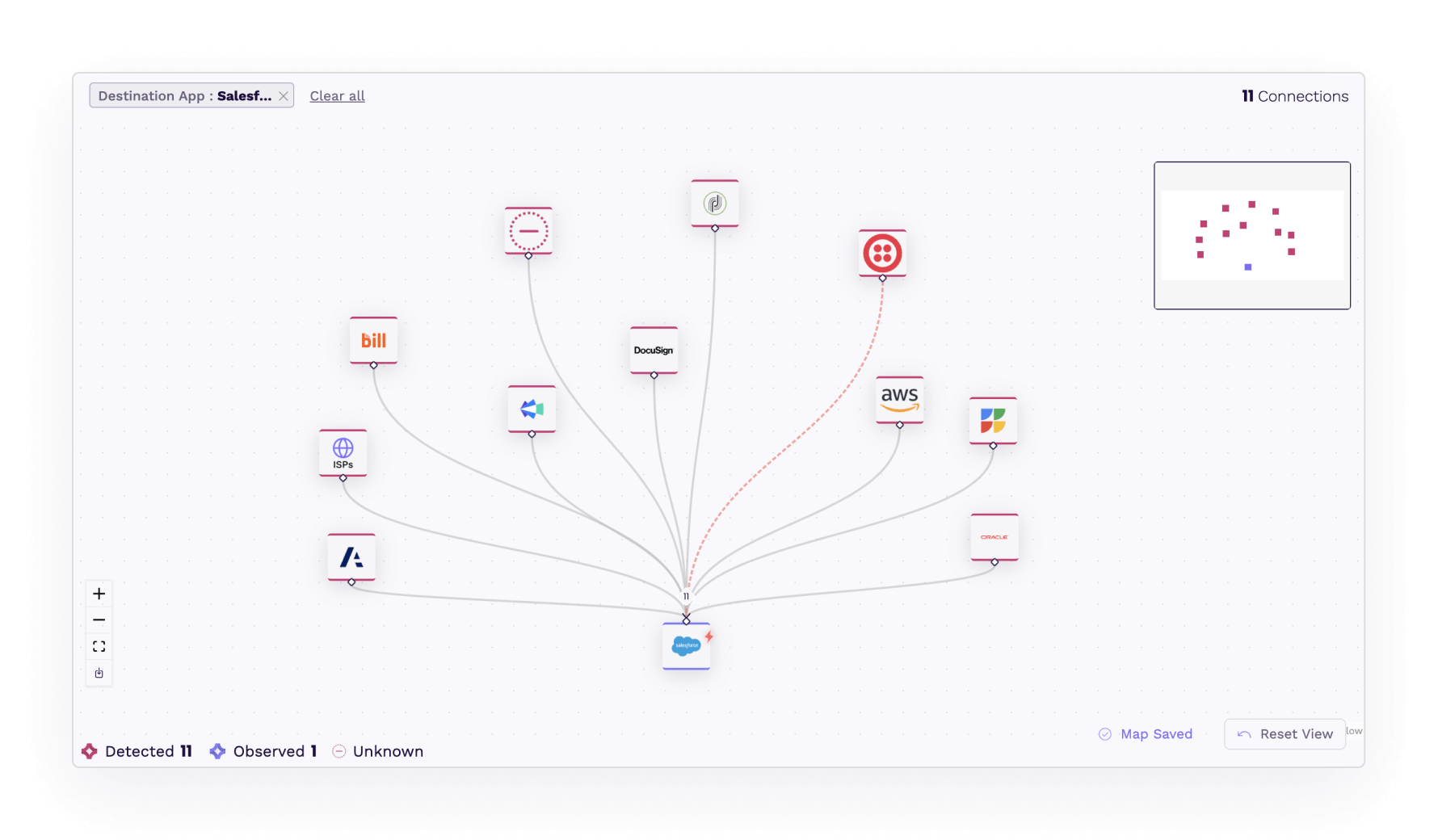
Breach Scoping and Investigation
Visualize all SaaS apps and connected services touching your organization's sensitive data.
Assess the impact of a SaaS breach and recover.
Understand how your sensitive data flows across third, fourth, and fith-party apps.
Search for IOCs (indicators of compromise) and identify affected accounts and secrets.
Rotate affected accounts or secrets across all apps, ensuring seamless continuation of existing workflows.