Attack Surface Reduction
Reduce your third-party attack surface by proactively identifying third-party threats.

Putting The Control Back Into Data Controller
When your organization uses third-party apps, it’s important to understand your attack surface. Without comprehensive visibility into the apps accessing your data, you run the risk of undetected breaches and security issues. This blind spot leaves you vulnerable to cyber threats that could compromise sensitive data, disrupt operations, and damage your organization's reputation.
Third-Party Threat Discovery
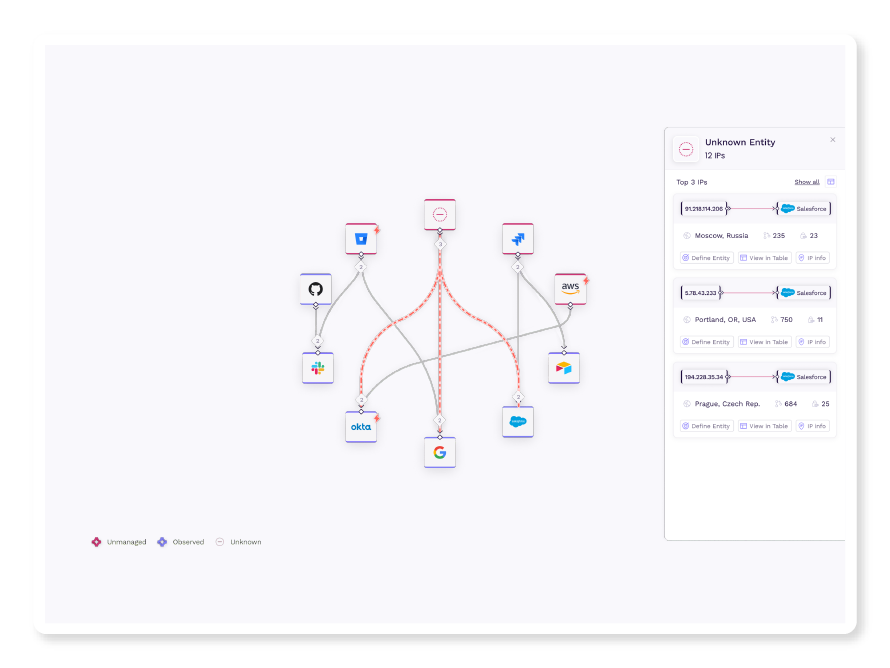
Vorlon maps your third-party app API landscape and discovers all of the third-party apps accessing your sensitive data. With continuous monitoring of your landscape, Vorlon exposes abnormal activity, bringing potential threats into focus and enabling swift response.
For security/incident response teams to understand their organization’s third-party attack surface.
Gain visibility into your entire third-party app ecosystem and understand which apps are accessing your sensitive data.
Quickly identify unusual or suspicious activities within your third-party apps.
Respond quickly and effectively to any security incidents.

Guide
Spin Cycle Security: Rotating Credentials
Learn best practices for setting rotation schedules based on risk levels, automating the rotation process for efficiency, and taking immediate action when workforce changes occur.