Supply Chain Security
Securing data in motion between third-party applications.

Monitor the Third-Parties in Your Supply Chain
When you have many third-party vendor relationships, your supply chain can get complicated fast. Each vendor brings their own systems, protocols, and potential vulnerabilities, creating a complex web. This complexity not only increases the risk of security breaches but also makes managing and monitoring these relationships a challenging task.
Third-Party Risk Analysis & Profiling
Vorlon conducts in-depth risk assessments of each third-party app, considering factors such as the app’s API design and the type of sensitive data the app transmits.
For CISOs, Compliance, and GRC teams to understand their third-party risk.
Get detailed reports and actionable insights into risks associated with third-party apps.
Quickly understand risk and stay proactive in managing the security and compliance of third-party apps.
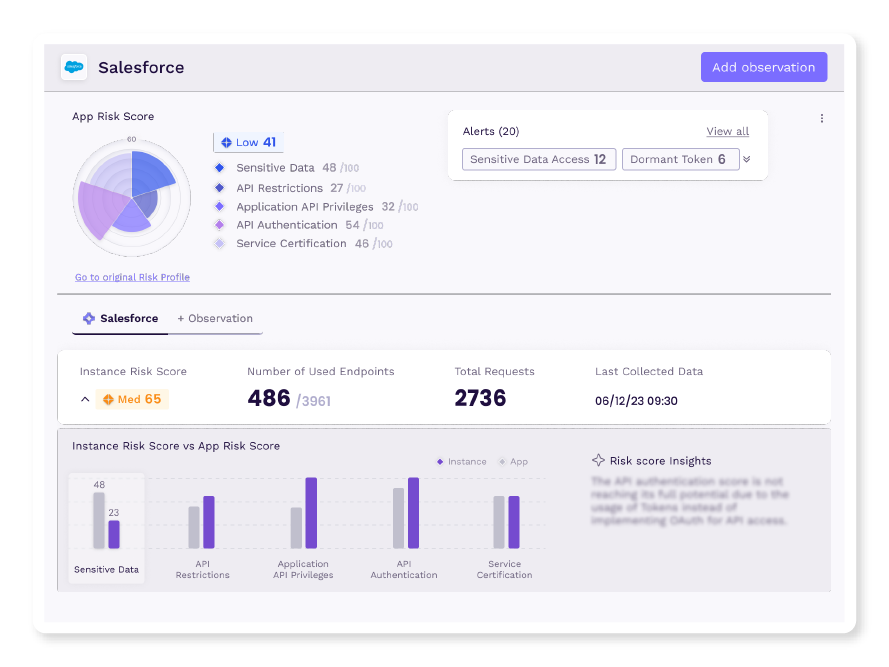
Vendor Compliance and Risk Monitoring
Vorlon continuously monitors, analyzes, and profiles third-party vendors. Compare the vendor's standardized risk score against your instance of the vendor's application and understand the compliance regulations required of the vendor.
For CISOs, Compliance, and GRC teams to understand vendor risk.
Understand each vendor with detailed profiles that include assessments of their security practice and potential risks.
Understand vendor risk and posture with standardized risk scoring.
Track vendor compliance regulations to ensure alignment with industry standards.
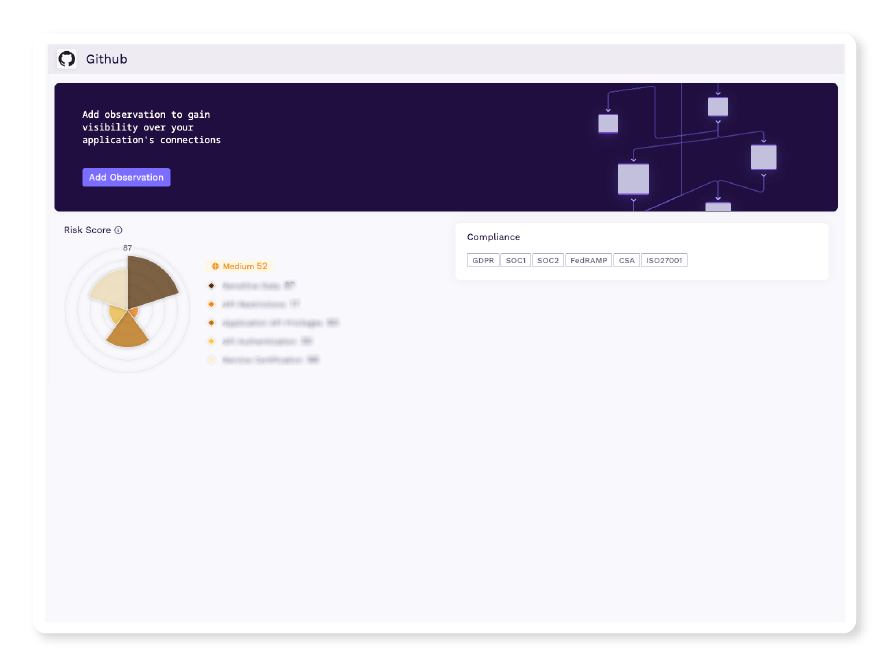
Understand Your Supply Chain
Data Privacy Teams
Proactively identify and mitigate privacy risks in your supply chain. Vorlon offers comprehensive monitoring and analysis of your entire vendor network, ensuring strict compliance with data privacy regulations.
CISOs/CIOs
Effectively communicate a coherent risk narrative to the board and stakeholders. Vorlon simplifies the complexity of third-party vendors into clear, actionable insights.
Compliance Teams
Ensure your organization consistently meets compliance obligations. Vorlon provides an all-encompassing view of regulatory requirements across your supply chain, ensuring adherence to industry standards and legal mandates.